Quick Start for Impatient
Configuration export from the gateway router:
'''/ ip address'''
add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local
add address=10.111.0.2/24 network=10.111.0.0 broadcast=10.111.0.255 interface=wlan2
add address=10.112.0.2/24 network=10.112.0.0 broadcast=10.112.0.255 interface=wlan1
'''/ ip firewall mangle'''
add chain=prerouting src-address-list=odd in-interface=Local action=mark-connection \
new-connection-mark=odd passthrough=yes
add chain=prerouting src-address-list=odd in-interface=Local action=mark-routing \
new-routing-mark=odd passthrough=no
add chain=prerouting src-address-list=even in-interface=Local action=mark-connection \
new-connection-mark=even passthrough=yes
add chain=prerouting src-address-list=even in-interface=Local action=mark-routing \
new-routing-mark=even passthrough=no
add chain=prerouting in-interface=Local connection-state=new nth=1,1,0 \
action=mark-connection new-connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=odd address-list-timeout=1d connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local connection-mark=odd action=mark-routing \
new-routing-mark=odd passthrough=no
add chain=prerouting in-interface=Local connection-state=new nth=1,1,1 \
action=mark-connection new-connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=even address-list-timeout=1d connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local connection-mark=even action=mark-routing \
new-routing-mark=even passthrough=no
'''/ ip firewall nat'''
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.111.0.2 \
to-ports=0-65535
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.112.0.2 \
to-ports=0-65535
'''/ ip route'''
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
[edit] Explanation
First we give a code snippet and then explain what it actually does.
[edit] IP Addresses
/ ip address
add address=192.168.0.1/24 network=192.168.0.0 broadcast=192.168.0.255 interface=Local
add address=10.111.0.2/24 network=10.111.0.0 broadcast=10.111.0.255 interface=wlan2
add address=10.112.0.2/24 network=10.112.0.0 broadcast=10.112.0.255 interface=wlan1
The router has two upstream (WAN) interfaces with the addresses of 10.111.0.2/24 and 10.112.0.2/24. The LAN interface has the name "Local" and IP address of 192.168.0.1/24.
[edit] Mangle
/ ip firewall mangle
add chain=prerouting src-address-list=odd in-interface=Local action=mark-connection \
new-connection-mark=odd passthrough=yes
add chain=prerouting src-address-list=odd in-interface=Local action=mark-routing \
new-routing-mark=odd
All traffic from customers having their IP address previously placed in the address list "odd" is instantly marked with connection and routing marks "odd". Afterwards the traffic is excluded from processing against successive mangle rules in prerouting chain.
/ ip firewall mangle
add chain=prerouting src-address-list=even in-interface=Local action=mark-connection \
new-connection-mark=even passthrough=yes
add chain=prerouting src-address-list=even in-interface=Local action=mark-routing \
new-routing-mark=even
Same stuff as above, only for customers having their IP address previously placed in the address list "even".
/ ip firewall mangle
add chain=prerouting in-interface=Local connection-state=new nth=1,1,0 \
action=mark-connection new-connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=odd address-list-timeout=1d connection-mark=odd passthrough=yes
add chain=prerouting in-interface=Local connection-mark=odd action=mark-routing \
new-routing-mark=odd passthrough=no
First we take every second packet that establishes new session (note connection-state=new), and mark it with connection mark "odd". Consequently all successive packets belonging to the same session will carry the connection mark "odd". Note that we are passing these packets to the second and third rules (passthrough=yes). Second rule adds IP address of the client to the address list to enable all successive sessions to go through the same gateway. Third rule places the routing mark "odd" on all packets that belong to the "odd" connection and stops processing all other mangle rules for these packets in prerouting chain.
/ ip firewall mangle
add chain=prerouting in-interface=Local connection-state=new nth=1,1,1 \
action=mark-connection new-connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local action=add-src-to-address-list \
address-list=even address-list-timeout=1d connection-mark=even passthrough=yes
add chain=prerouting in-interface=Local connection-mark=even action=mark-routing \
new-routing-mark=even passthrough=no
These rules do the same for the remaining half of the traffic as the first three rules for the first half of the traffic.
The code above effectively means that each new connection initiated through the router from the local network will be marked as either "odd" or "even" with both routing and connection marks.
The above works fine. There are however some situations where you might find that the same IP address is listed under both the ODD and EVEN scr-address-lists. This behavior causes issues with apps that require persistent connections. A simple remedy for this situation is to add the following statement to your mangle rules:
add chain=prerouting in-interface=Local connection-state=new nth=1,1,1 \
src-address-list=!odd action=mark-connection new-connection-mark=even \
passthrough=yes
This will ensure that the new connection will not already be part of the ODD src-address-list. You will have to do the same for the ODD mangle rule thus excluding IP's already part of the EVEN scr-address-list.
[edit] NAT
/ ip firewall nat
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.111.0.2 \
to-ports=0-65535
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.112.0.2 \
to-ports=0-65535
All traffic marked "odd" is being NATted to source IP address of 10.111.0.2, while traffic marked "even" gets "10.112.0.2" source IP address.
[edit] Routing
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even
For all traffic marked "odd" (consequently having 10.111.0.2 translated source address) we use 10.111.0.1 gateway. In the same manner all traffic marked "even" is routed through the 10.112.0.1 gateway.
/ ip route
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
Finally, we have one additional entry specifying that traffic from the router itself (the traffic without any routing marks) should go to 10.112.0.1 gateway.
source:http://wiki.mikrotik.com/wiki/Load_Balancing_Persistent
Kamis, 24 April 2008
Load Balancing Persistent
Two gateways failover with load balancing
Route
According to the examples above, you have:
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
Now you have to change these lines to:
/ ip route
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 routing-mark=odd check-gateway=ping
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10 routing-mark=even check-gateway=ping
add dst-address=0.0.0.0/0 gateway=10.112.0.1 scope=255 target-scope=10
add dst-address=0.0.0.0/0 gateway=10.111.0.1 scope=255 target-scope=10 distance=2
If ping fails to 10.111.0.1, then all traffic marked odd go's to the gateway 10.112.0.1, the oposite is also true.
All local traffic go's to the 10.112.0.1 as it's distance is smaller, if 10.112.0.1 fails, then 10.111.0.1 takes over.
The router pings gateway every 10 seconds and if to consecutive pings to the gateway fail, the route is considered dead. So, then testing keep in mind, that gateway failure is detected in 20 to 30 seconds.
[edit] NAT
/ ip firewall nat
add chain=srcnat connection-mark=odd action=src-nat to-addresses=10.111.0.2 \
to-ports=0-65535 comment="" disabled=no
add chain=srcnat connection-mark=even action=src-nat to-addresses=10.112.0.2 \
to-ports=0-65535 comment="" disabled=no
change to:
/ip firewall nat
add chain=srcnat src-address=192.168.0.0/24 action=masquerade
source:http://wiki.mikrotik.com/wiki/Two_gateways_failover_with_load_balancing
Jumat, 11 April 2008
Memisahkan gateway traffic Local dan International
/ ip address
add address=203.89.24.66/27 network=203.89.24.64 broadcast=203.89.24.95 \
interface=ether1 comment=”ip point to point utk traffic lnternational” \
disabled=no
add address=203.89.24.178/30 network=203.89.24.176 broadcast=203.89.24.179 \
interface=ether1 comment=”ip point to point utk traffic local” disabled=no
/ ip firewall address-list
add list=nice address=58.65.240.0/23 comment=”” disabled=no
add list=nice address=58.65.242.0/23 comment=”” disabled=no
add list=nice address=58.65.244.0/23 comment=”” disabled=no
add list=nice address=58.65.246.0/23 comment=”” disabled=no
add list=nice address=58.145.174.0/24 comment=”” disabled=no
add list=nice address=58.147.184.0/24 comment=”” disabled=no
add list=nice address=58.147.185.0/24 comment=”” disabled=no
dst…
/ ip firewall mangle
add chain=postrouting dst-address-list=nice action=mark-routing \
new-routing-mark=nice passthrough=yes comment=”” disabled=no
/ ip route
add dst-address=0.0.0.0/0 gateway=203.89.24.65 scope=255 target-scope=10 \
comment=”traffic selain local Indonesia” disabled=no
add dst-address=0.0.0.0/0 gateway=203.89.24.177 scope=255 target-scope=10 \
routing-mark=nice comment=”traffic local Indonesia” disabled=no
Sabtu, 08 Maret 2008
EoIP
Quick Setup Guide
To make an EoIP tunnel between 2 routers which have IP addresses 10.5.8.1 and 10.1.0.1:
1.
On router with IP address 10.5.8.1, add an EoIP interface and set its MAC address:
/interface eoip add remote-address=10.1.0.1 tunnel-id=1 mac-address=00-00-5E-80-00-01 \
\... disabled=no
2.
On router with IP address 10.1.0.1, add an EoIP interface and set its MAC address::
/interface eoip add remote-address=10.5.8.1 tunnel-id=1 mac-address=00-00-5E-80-00-02 \
\... disabled=no
Now you can add IP addresses to the created EoIP interfaces from the same subnet.
EoIP Application Example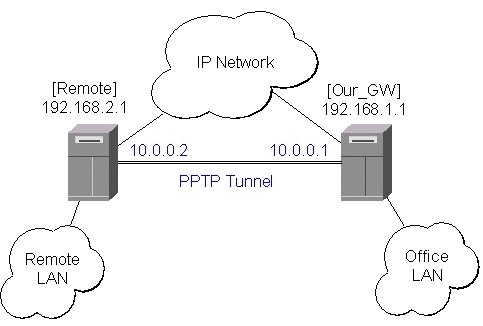
To make a secure Ethernet bridge between two routers you should:
1.
Create a PPTP tunnel between them. Our_GW will be the pptp server:
[admin@Our_GW] interface pptp-server> /ppp secret add name=joe service=pptp \
\... password=top_s3 local-address=10.0.0.1 remote-address=10.0.0.2
[admin@Our_GW] interface pptp-server> add name=from_remote user=joe
[admin@Our_GW] interface pptp-server> server set enable=yes
[admin@Our_GW] interface pptp-server> print
Flags: X - disabled, D - dynamic, R - running
# NAME USER MTU CLIENT-AD... UPTIME ENCODING
0 from_remote joe
[admin@Our_GW] interface pptp-server>
The Remote router will be the pptp client:
[admin@Remote] interface pptp-client> add name=pptp user=joe \
\... connect-to=192.168.1.1 password=top_s3 mtu=1500 mru=1500
[admin@Remote] interface pptp-client> enable pptp
[admin@Remote] interface pptp-client> print
Flags: X - disabled, R - running
0 R name="pptp" mtu=1500 mru=1500 connect-to=192.168.1.1 user="joe"
password="top_s2" profile=default add-default-route=no
[admin@Remote] interface pptp-client> monitor pptp
status: "connected"
uptime: 39m46s
encoding: "none"
[admin@Remote] interface pptp-client>
See the PPTP Interface Manual for more details on setting up encrypted channels.
2.
Configure the EoIP tunnel by adding the eoip tunnel interfaces at both routers. Use the ip addresses of the pptp tunnel interfaces when specifying the argument values for the EoIP tunnel:
[admin@Our_GW] interface eoip> add name="eoip-remote" tunnel-id=0 \
\... remote-address=10.0.0.2
[admin@Our_GW] interface eoip> enable eoip-remote
[admin@Our_GW] interface eoip> print
Flags: X - disabled, R - running
0 name=eoip-remote mtu=1500 arp=enabled remote-address=10.0.0.2 tunnel-id=0
[admin@Our_GW] interface eoip>
[admin@Remote] interface eoip> add name="eoip" tunnel-id=0 \
\... remote-address=10.0.0.1
[admin@Remote] interface eoip> enable eoip-main
[admin@Remote] interface eoip> print
Flags: X - disabled, R - running
0 name=eoip mtu=1500 arp=enabled remote-address=10.0.0.1 tunnel-id=0
[Remote] interface eoip>
3.
Enable bridging between the EoIP and Ethernet interfaces on both routers.
On the Our_GW:
[admin@Our_GW] interface bridge> add
[admin@Our_GW] interface bridge> print
Flags: X - disabled, R - running
0 R name="bridge1" mtu=1500 arp=enabled mac-address=00:00:00:00:00:00
protocol-mode=none priority=0x8000 auto-mac=yes
admin-mac=00:00:00:00:00:00 max-message-age=20s forward-delay=15s
transmit-hold-count=6 ageing-time=5m
[admin@Our_GW] interface bridge> port add bridge=bridge1 interface=eoip-remote
[admin@Our_GW] interface bridge> port add bridge=bridge1 interface=office-eth
[admin@Our_GW] interface bridge> port print
Flags: X - disabled, I - inactive, D - dynamic
# INTERFACE BRIDGE PRIORITY PATH-COST
0 eoip-remote bridge1 128 10
1 office-eth bridge1 128 10
[admin@Our_GW] interface bridge>
And the same for the Remote:
[admin@Remote] interface bridge> add
[admin@Remote] interface bridge> print
Flags: X - disabled, R - running
0 R name="bridge1" mtu=1500 arp=enabled mac-address=00:00:00:00:00:00
protocol-mode=none priority=0x8000 auto-mac=yes
admin-mac=00:00:00:00:00:00 max-message-age=20s forward-delay=15s
transmit-hold-count=6 ageing-time=5m
[admin@Remote] interface bridge> port add bridge=bridge1 interface=ether
[admin@Remote] interface bridge> port add bridge=bridge1 interface=eoip-main
[admin@Remote] interface bridge> port print
Flags: X - disabled, I - inactive, D - dynamic
# INTERFACE BRIDGE PRIORITY PATH-COST
0 ether bridge1 128 10
1 eoip-main bridge1 128 10
[admin@Remote] interface bridge>
4. Addresses from the same network can be used both in the Office LAN and in the Remote LAN.
source: http://www.mikrotik.com/testdocs/ros/3.0/vpn/eoip.php
Minggu, 02 Maret 2008
Routing Questions
Question: How does /ip route check-gateway work?
check-gateway sends pings every 10 seconds. if two successive pings fail, the gateway is considered dead.
Question: I have one /24 network advertised to two BGP peers using "/routing bgp networks" facility. How do I advertise a higher path cost to one of the peers?
You have to change the way you are redistributing your network, as filters are not applied to routes advertised from "/routing bgp networks". In most cases the network is connected directly to your router, so it's enough to set BGP instance to redistribute directly connected routes:
/routing bgp instance set default redistribute-connected=yes
To filter out all other connected networks except the needed one, create a routing filter for the BGP instance,
/routing filter add invert-match=yes prefix=10.0.0.0/24 action=discard name=InstanceOutFilter
then set filter "InstanceOutFilter" as the out-filter for "default" BGP instance.
/routing bgp instance set default out-filter=InstanceOutFilter
To communicate a lower preference value (higher path cost) to one of the peers, you have to prepend your AS number multiple times to the BGP AS_PATH attribute
/routing filter add prefix=10.0.0.0/24 set-bgp-prepend=4 name=Peer1OutFilter
/routing bgp peer set Peer1 out-filter=Peer1OutFilter
Question: I have a /22 (say 10.0.0.0/22) assigned IP space, split internally down into /30's, /28's, etc. Is it possible just to announce the /22 space via BGP with routing-test package?
Yes, it is possible. Do the following:
1. add an empty bridge interface:
/interface bridge add name=loopback
2. assign a /22 address to the bridge interface:
/ip address add address=10.0.0.1/22 interface=loopback
3. create a routing filter that filters out all prefixes except the /22 one
/routing filter add invert-match=yes prefix=10.0.0.0/22 prefix-length=22 action=discard name=myfilter
4. set filter "myfilter" as the out-filter for "default" BGP instance
/routing bgp instance set default out-filter=myfilter
Question: How to blackhole a network?
There are two ways to blackhole a network. First, you can do this manually by adding a blackhole route to the routing table, for example, to blackhole a 10.0.0.0/8 network, issue the following command:
/ip route add dst-address=10.0.0.0/8 kernel-type=blackhole
Routing filters are the other mean to blackhole a network. To create a routing filter that automatically blackholes all prefixes in 10.0.0.0/8 in the BGP feed, issue the following command:
/routing filter add prefix=10.0.0.0/8 prefix-length=8-32 set-kernel-type=blackhole chain=myfilter
Question: How to filter out the default route from outgoing BGP advertisements?
Assuming you have a static default route that is redistributed because redistribute-static parameter is set to yes, do the following:
/routing filter add chain=myfilter prefix=0.0.0.0/0 action=discard
Then set myfilter as the out-filter for BGP instance
/routing bgp instance set default out-filter=myfilter
Kamis, 28 Februari 2008
Rabu, 27 Februari 2008
Transparent Traffic Shaper
This example shows how to configure a transparent traffic shaper. The transparent traffic shaper is essentially a bridge that is able to differentiate and prioritize traffic that passes through it.
Consider the following network layout:

We will configure one queue limiting the total throughput to the client and three sub-queues that limit HTTP, P2P and all other traffic separately.
Quick Start for Impatient
Configuration snippet from the MikroTik router:
/ interface bridge
add name="bridge1"
/ interface bridge port
add interface=ether2 bridge=bridge1
add interface=ether3 bridge=bridge1
/ ip firewall mangle
add chain=prerouting protocol=tcp dst-port=80 action=mark-connection \
new-connection-mark=http_conn passthrough=yes
add chain=prerouting connection-mark=http_conn action=mark-packet \
new-packet-mark=http passthrough=no
add chain=prerouting p2p=all-p2p action=mark-connection \
new-connection-mark=p2p_conn passthrough=yes
add chain=prerouting connection-mark=p2p_conn action=mark-packet \
new-packet-mark=p2p passthrough=no
add chain=prerouting action=mark-connection new-connection-mark=other_conn \
passthrough=yes
add chain=prerouting connection-mark=other_conn action=mark-packet \
new-packet-mark=other passthrough=no
/ queue simple
add name="main" target-addresses=10.0.0.12/32 max-limit=256000/512000
add name="http" parent=main packet-marks=http max-limit=240000/500000
add name="p2p" parent=main packet-marks=p2p max-limit=64000/64000
add name="other" parent=main packet-marks=other max-limit=128000/128000
Explanation
Each piece of code is followed by the explanation of what it actually does.
Bridge
/ interface bridge
add name="bridge1"
/ interface bridge port
add interface=ether2 bridge=bridge1
add interface=ether3 bridge=bridge1
We create a new bridge interface and assign two ethernet interfaces to it. Thus the prospective traffic shaper will be completely transparent to the client.
Mangle
/ ip firewall mangle
add chain=prerouting protocol=tcp dst-port=80 action=mark-connection \
new-connection-mark=http_conn passthrough=yes
add chain=prerouting connection-mark=http_conn action=mark-packet \
new-packet-mark=http passthrough=no
All traffic destined to TCP port 80 is likely to be HTTP traffic and therefore is being marked with the packet mark http. Note, that the first rule has passthrough=yes while the second one has passthrough=no. (You can obtain additional information about mangle at http://www.mikrotik.com/docs/ros/2.9/ip/mangle)
/ ip firewall mangle
add chain=prerouting p2p=all-p2p action=mark-connection \
new-connection-mark=p2p_conn passthrough=yes
add chain=prerouting connection-mark=p2p_conn action=mark-packet \
new-packet-mark=p2p passthrough=no
add chain=prerouting action=mark-connection new-connection-mark=other_conn \
passthrough=yes
add chain=prerouting connection-mark=other_conn action=mark-packet \
new-packet-mark=other passthrough=no
Same as above, P2P traffic is marked with the packet mark p2p and all other traffic is marked with the packet mark other.
Queues
/ queue simple
add name="main" target-addresses=10.0.0.12/32 max-limit=256000/512000
We create a queue that limits all the traffic going to/from the client (specified by the target-address) to 256k/512k.
/ queue simple
add name="http" parent=main packet-marks=http max-limit=240000/500000
add name="p2p" parent=main packet-marks=p2p max-limit=64000/64000
add name="other" parent=main packet-marks=other max-limit=128000/128000
All sub-queues have the main queue as the parent, thus the aggregate data rate could not exceed limits specified in the main queue. Note, that http queue has higher priority than other queues, meaning that HTTP downloads are prioritized.
source http://wiki.mikrotik.com/wiki/TransparentTrafficShaper